This blog will contain the information that you need to get started with an SSH connection, enjoy!
INSTALLATION
To install SSH on Linux, start with updating the system.
sudo apt update
For Debian systems use the following commands.
sudo apt install openssh-server
sudo apt install openssh-client
And finally, you can start the SSH service.
sudo service ssh start
Notice how we installed the OpenSSH server and client. That way we will be able to connect to a server using SSH, and other computers to connect to our computer using the necessary credentials making it a server.
SECURE SHELL (SSH)
It is a network protocol and cryptographic technology used for secure communication and remote access over an unsecured network. It is used to provide security during data transmission. It provides tools like SCP and SFTP for secure copy protocol and SSH file transfer protocol. One of the cool things about it is that it creates a secure tunnel for clients to access remote services on remote servers. You might wonder what services can we access with SSH. The services range from email, web, and database connections... One thing to note is that it is not possible to just log into a machine using SSH without it containing an OPEN SSH DAEMON.
OPEN SSH DAEMON (SSHD)
An important component of the OpenSSH software suite. It runs on a server and allows secure remote access and communication using SSH protocol. It is responsible for the following:
Securing access: It listens for SSH connections and manages its secure remote access to a server.
Authentication: At the connection of a client to the server, the SSHD allows authentication either by password or a key (SSH key pair).
Encryption: One of the SSHD's responsibilities is the encryption of the communication between the client and the server.
Access control: The SSHD can allow or deny access to users based on pre-configurations set by administrators. The access can be filtered based on usernames and IP addresses ...
Port: By default, the SSH listens on port 22 for incoming connections, however, it can still be configured.
Keeping log: The SSHD keeps a log of activities that can be monitored. The log file can be found in
/var/log/auth.log.
SSH CONFIGURATION FILE
It is a plain text file containing the configurations used by the SSH client and server. It is located in ~/.ssh or the /etc/ssh folder. Keep in mind each SSH server and SSH client has a configuration file. For the server, it is called sshd_config while for the client it is called ssh_config. Try to display both their content.
cat /etc/ssh/ssh_config
cat /etc/ssh/sshd_config
Here is a simple SSH config file.
# Global settings (apply to all hosts)
Host *
Port 2222 # Use port 2222 for all SSH connections
User john # Default username
# Default private key for authentication
IdentityFile ~/.ssh/my_key
# Custom settings for specific hosts
Host example.com
HostName example.com # Hostname or IP address
User alice # Specific username for this host
# Private key for this host
IdentityFile ~/.ssh/alice_key
AUTHENTICATION
To authenticate with the server you can follow the password method which is the default, or the key method. To authenticate with a server use this command:
ssh user@hostName # Host name or the ip address
If after this command you were prompted with the password that is because you didn't set up the SSH key. If you were prompted with a message saying: Are you sure you want to continue connecting say yes. It will be the last time you'll see this message 🧙♂️. And ta-da, now you are using a server✨. Type exit to get out. To make it easier for you, we should set up the SSH key, that way you won't have to use the stupid password again. It is not only easier and much more efficient, but it is also safer because the password can be brute forced. To set up your SSH key follow these steps.
ssh-keygen
This command will generate two keys for you.
☝️ Private RSA key. [id_rsa]
✌️ Public RSA key. [id_rsa.pub]
Don't worry about RSA I will explain that later and you are going to love it.
ssh-keygen -f Mykey -N "secret" -b 4096
This command will generate a key containing 4094 bits, add a passphrase "secret", and save the keys under the name Mykey.
PassPhrases are used to add a layer of security. They are used to protect cryptographic keys. They are similar to passwords but are typically longer and more complex.
If you want to check the keys created, they will be in your home folder in the /.ssh folder. The (.) means it is a hidden folder.
cat ~/.ssh/id_rsa
cat ~/.ssh/id_rsa.pub
In the same folder, /.ssh you will find another cool thing. The authorized_keys file. Your public key will be in there. If it doesn't exist you can create it. It is a file that keeps the authorized keys of machines that are granted access. Next, you want to either authenticate with the public key to the server or copy your public key and add it to the authorized keys in the server. To Authenticate without copying the key:
ssh -i ~/.ssh/id_rsa.pub user@hostName
To copy the key to the server:
cat ~/.ssh/id_rsa.pub | ssh brad@192.168.1.29 "mkdir" -p ~/.ssh && chmod 700 ~/.ssh && cat >> ~/.ssh/authorized_keys
This command is simple, it caters to your public key, takes the output, and connects to the server using SSH. Then create a directory (the -p option makes sure that any parents of the directory required for the path will be created if they don't exist). the /.ssh is then given the following permission: 700 = rwx ___ ___, allowing only the user (owner) to have all the rights. And then the public key is appended to the authorized_keys file (>> is to append and > is to replace). Another way to copy files to the remote server is by using a secure copy.
# Exit from the server.
touch testFile
scp ~/testFile user@hostName:~ # To put it in the HOME ~
Remember SSH is a very secure protocol, but to enhance its security, you can do SSH key rotation. Which is a name for periodically changing the SSH key on the remote server.
SECURE FILE TRANSFER PROTOCOL
It is an encrypted file transfer protocol used for transferring files and managing remote file systems over a secure channel, over SSH connection. I am sure you heard of FTP, the protocol that transmits data in plain text, well, SFTP is what you call a secure alternative since it encrypts the transferred data. To open an interactive SFTP session use this command.
sftp user@hostName
You will then be prompted with :
Connected to hostname.
sftp>
You are now able to perform any file transfer operation. The following are a few of the operations.
- File upload: You can upload files to the remote server from your computer using the put.
put file.txt
- File download: You can get files from the server by using get.
get file.txt
List content: While in the SFTP mode, you can list the content of the remote server using ls.
Change directory: You can navigate directories normally, using cd. You can use the shell commands.
Exit SFTP: Use exit, or even better, use bye 👋.
CRYPTOGRAPHIC ALGORITHMS
SSH uses a set of cryptographic algorithms. These algorithms are used for various purposes within SSH. Here is a list of the things that require encryption, and the algorithms used in each.
Key exchange: Elliptic Curve Diffie-Hellman (ECDH) It is a variant of the Diffie-Hellman key exchange algorithm, offering strong security with a small size, the common ECDH sizes include (256-bit, 384-bit, 521 bit)
Encryption: SSH uses symmetric encryption to encrypt the transferred data. AES Advanced Encryption Standard Is an algorithm used for that purpose. 3DES Triple Data Encryption Standard An older variant that is less commonly used for SSH configurations.
Message authentication code: HMAC Hash-based Message Authentication
Public key: RSA Rivest Shamir-Adleman It is used for public key-based authentication. Ed25519 It is an elliptic curve digital signature algorithm used for authentication in SSH.
SSH uses different algorithms at each stage of the connection to ensure security, integrity, and authentication.
RSA ENCRYPTION
Time to learn about RSA😋. Invented by Ron Rivest, Adi Shamir, and Leonard Adleman. It is an encryption algorithm.
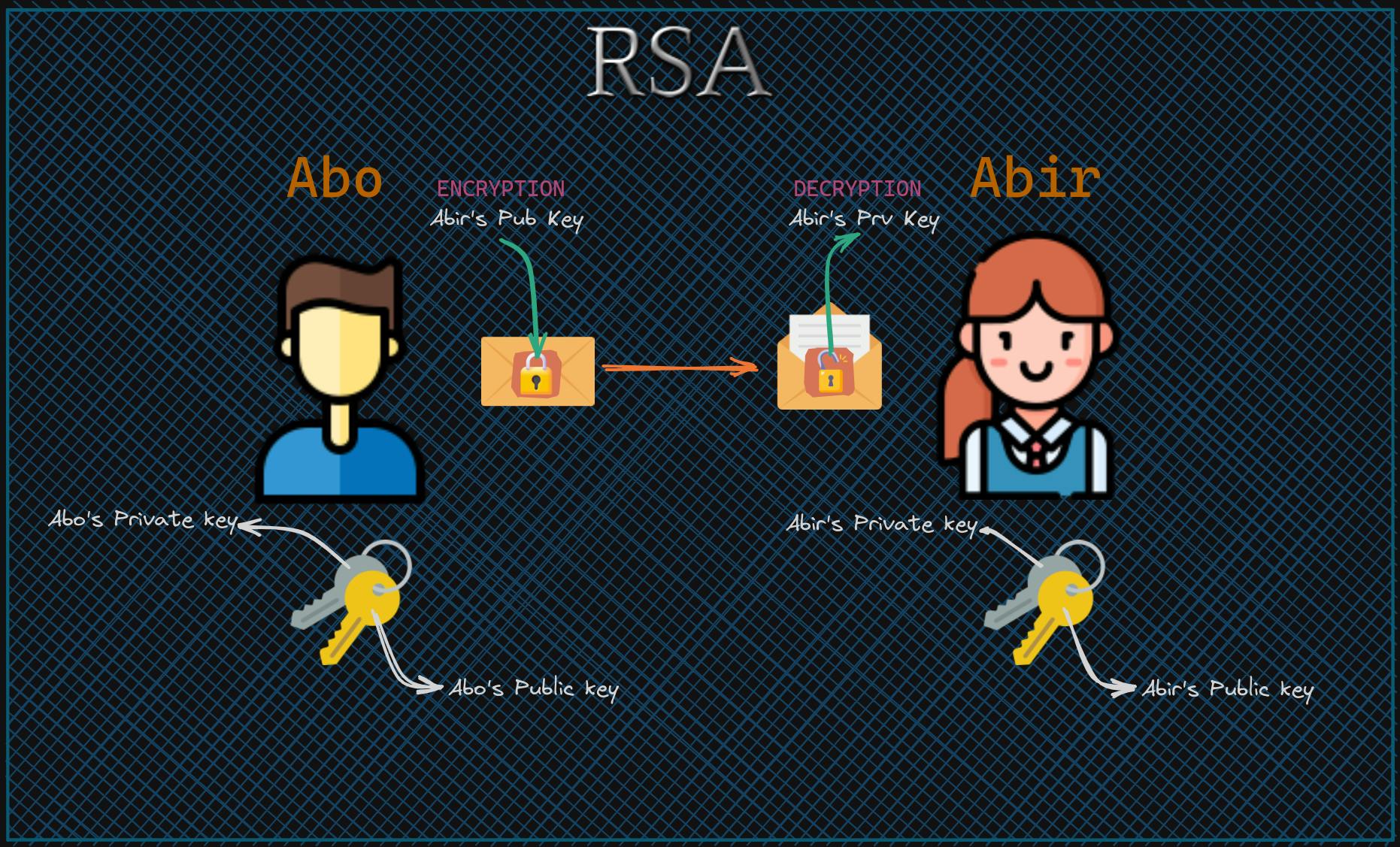
A simple way of looking at how this works is the following. Abo is a person who wants to send a message to a person named Abir. Abir has generated two keys, one public and another private. Abo will encrypt the message he wants to send to Abir, he encrypts it using the public key of Abir. Sends the message, then Abir will decrypt it using the private key and reads the message. How is that possible that the message was encrypted using a key just to be decrypted using a different key? Well, the two keys that Abir generated use two mathematically related keys. The Strength of RSA encryption depends on the size of the key (number of bits).
This DevOps topic is really interesting, especially the interesting s cryptography part. Really tuff. See you in the next one. I'll leave you with this quote that we stay with longer.
It is not that I’m so smart. But I stay with the questions much longer.
Albert Einstein
IMPORTANT RESOURCES
WinScp [SSH GUI] https://winscp.net/eng/download.php
FileZilla [Ftp client GUI] https://filezilla-project.org/
SSHCheatSheet [The SSH commands] https://gist.github.com/bradtraversy/f03df587f2323b50beb4250520089a9e


